原创文章,转载请指明出处并保留原文url地址
本文主要针对nginx的ngx_http_auth_basic_module模块做简单介绍,本文具体包括如下指令:auth_basic,auth_basic_user_file
ngx_http_auth_basic_module
模块通过http的基本验证协议通过用户及密码的方式来验证用户是否具有对某些资源的访问权限。
用户的访问可以通过ip地址进行限制。访问控制也可以通过ip地址及密码控制同时存在的方式进行。
Nginx原文:
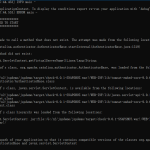
Example Configuration
location / {
auth_basic "closed site";
auth_basic_user_file conf/htpasswd;
}
The ngx_http_auth_basic_module module allows to limit access to resources by validating the user name and password using the “HTTP Basic Authentication” protocol.
Access can also be limited by address. Simultaneous limitation of access by address and by password is controlled by the satisfy directive.
Example Configuration
location / {
auth_basic "closed site";
auth_basic_user_file conf/htpasswd;
}
1. auth_basic
| syntax: | auth_basic string| off; |
| default: | auth_basic off; |
| context: | http, server, location, limit_except |
允许使用“HTTP基本身份验证”协议的用户名和密码的验证。指定的参数被用作一种境界。参数的值可以包含变量(1.3.10)。参数off可以取消继承于前面配置的auth_basic指令的影响。
Nginx原文:
Enables validation of user name and password using the “HTTP Basic Authentication” protocol. The specified parameter is used as a realm. Value of the parameter can contain variables (1.3.10). The special value off allows to cancel the effect of the auth_basic directive inherited from the previous configuration level.
2. auth_basic_user_file
| syntax: | auth_basic_user_file file; |
| default: | — |
| context: | http, server, location, limit_except |
指定一个文件来保存用户名及密码,格式如下:
#注释
NAME1:密码
NAME2:密码:注释
NAME3:密码
下面是被支持的密码类型:
用crypt()函数加密的;从apache server分发版本后者openssl passwd命令产生的密码。
Apache的基于apr1算法的md5变种hash值,或者相同空间产生的。
RFC 2307中描述指定的“{方案}”语法(1.0.3+),目前正在实施的计划包括平原(例如,不应该被使用)和SSHA(咸SHA-1散列,使用一些软件软件包,如著名的OpenLDAP和Dovecot)。
Nginx原文:
Specifies a file that keeps user names and passwords, in the following format:
# comment
name1:password1
name2:password2:comment
name3:password3
The following password types are supported:
encrypted with the crypt() function; can be generated using the “htpasswd” utility from the Apache HTTP Server distribution or the “openssl passwd” command;
hashed with the Apache variant of the MD5-based password algorithm (apr1); can be generated with the same tools;
specified by the “{scheme}data” syntax (1.0.3+) as described in RFC 2307; currently implemented schemes include PLAIN (an example one, should not be used) and SSHA (salted SHA-1 hashing, used by some software packages, notably OpenLDAP and Dovecot).